Overview
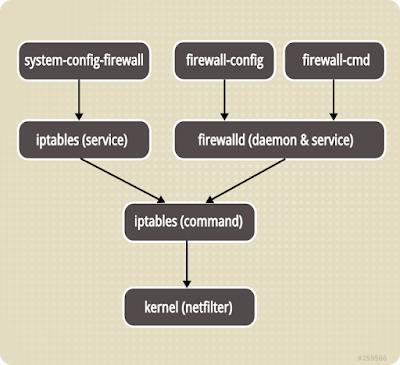
firewall-cmd
Everything in firewalld are organized in zones.
| --list-all-zones | List everything for every zones. | --get-active-zones | Print currently active zones altogether with interfaces and sources used in these zones. |
| --get-default-zone | Print default zone for connections and interfaces. |
| --set-default-zone=<ZONE> | Set default zone for connections and interfaces. |
| --add-source= | Bind source to zone. |
| --remove-source= | Unbind source to zone. |
| --add-interface= | Bind interface to zone. |
| --change-interface= | Bind interface to different zone. |
Comments for zones from RHEL 7 Security Guide Using Firewalls.
| public | For use in public areas. You do not trust the other computers on the network to not harm your computer. Only selected incoming connections are accepted. |
| external | For use on external networks with masquerading enabled especially for routers. You do not trust the other computers on the network to not harm your computer. Only selected incoming connections are accepted. |
| dmz | For computers in your demilitarized zone that are publicly-accessible with limited access to your internal network. Only selected incoming connections are accepted. |
| work | For use in work areas. You mostly trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted. |
| home | For use in home areas. You mostly trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted. |
| internal | For use on internal networks. You mostly trust the other computers on the networks to not harm your computer. Only selected incoming connections are accepted. |
| trusted | All network connections are accepted. |
Below are commands to alter firewall. All command are only added in runtime and first adding options --permanent while it be written to disk and made permanent.
| --get-services | List all predefined services. |
| --add-service= | Open/allow traffic to service. |
| --remove-service= | Remove/deny traffic to serice |
| --add-port= | Open/allow traffic on port and protocol. |
| --remove-port= | Remove/deny on port and protocol. |
| --reload | Reload persistent rules from /usr/lib/firewalld/ and /etc/firewalld/. |
Examples